Signed in as:
filler@godaddy.com
Signed in as:
filler@godaddy.com
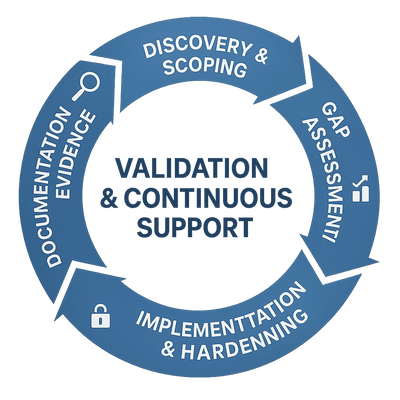
We begin by understanding your business structure, regulatory exposure (e.g., FCI, CUI), IT environment, and organizational goals. This phase defines the system boundary and establishes the scope for your compliance engagement.
Your current practices are assessed against the selected framework. We identify which requirements are met, which are missing, and the level of effort required to close each gap.
Based on your gap assessment, we build a prioritized, risk-based roadmap to remediation. This includes technical fixes, policy development, training needs, and timelines. For CMMC, a draft POA&M is also created to guide implementation.
We apply technical controls (e.g., secure Wi-Fi, access controls, backup configs), administrative safeguards (e.g., policies, training), and system hardening to align your environment with required controls.
We prepare or update critical compliance documents: System Security Plan (SSP), policies, POA&M, training logs, access control lists, and other audit-ready artifacts.
A final review ensures all practices are addressed, and evidence is validated. Optional vCISO advisory, policy refresh, or annual re-validation services are available to maintain compliance over time.
Get expert advice and guidance on cybersecurity from our team of experts. We offer cybersecurity consulting services to help you identify and manage your cybersecurity risks.
We use cookies to analyze website traffic and optimize your website experience. By accepting our use of cookies, your data will be aggregated with all other user data.